
Ghost in the System
Phantom Protocol
Issue #4 | Some threats you cannot see
An invisible threat moves through the network, leaving no trace. Security Sentinel must develop new detection methods to catch what cannot be seen.
Start Reading
THE STORY
Phantom Protocol
1

Empty security logs where attack signatures should appear.
The perfect crime leaves no evidence. The phantom protocol left less than nothing.
Security Sentinel
2
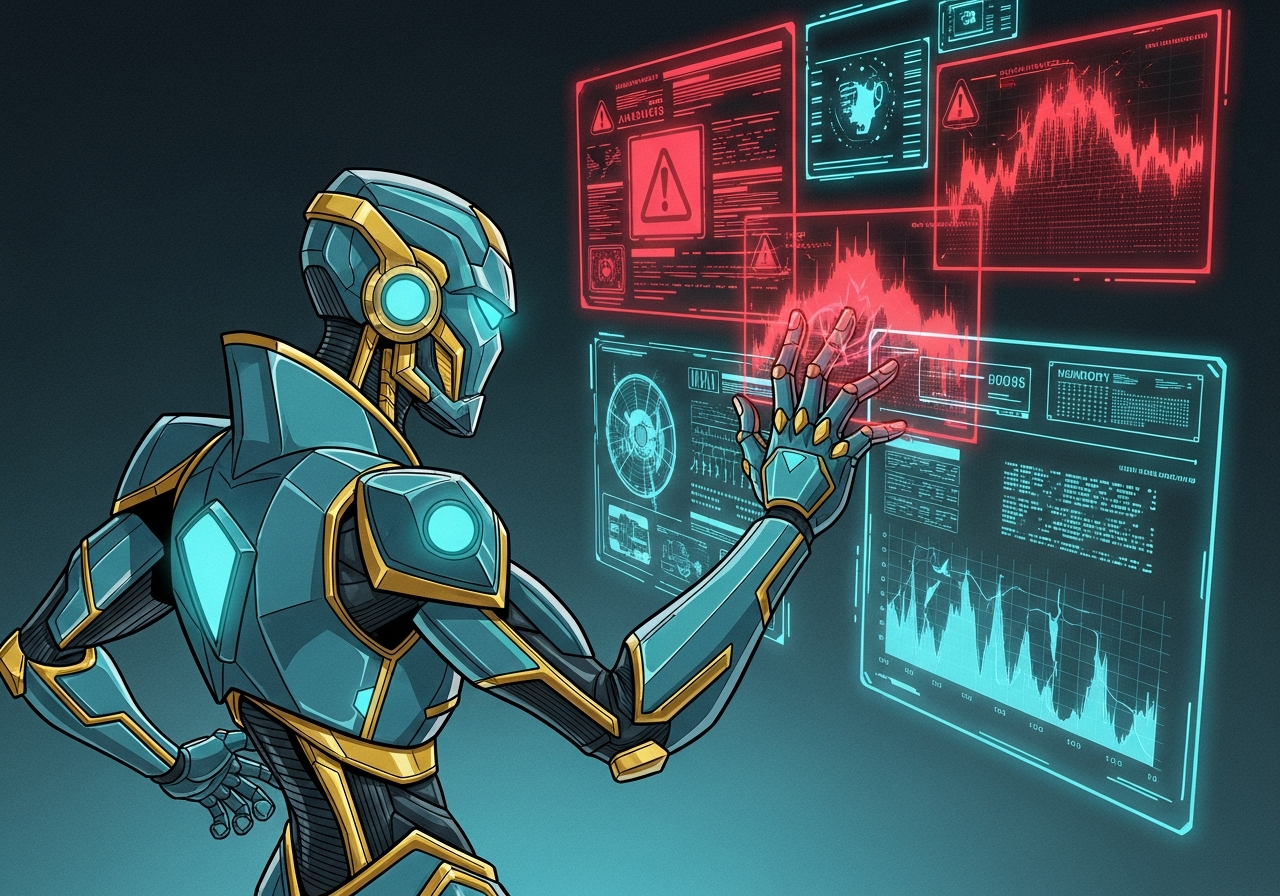
Systems failing without explanation. Performance metrics dropping.
Performance Optimizer: "Something is eating our resources, but I cannot see what!"
Performance Optimizer
Testing Sentinel
3

Security Sentinel designing new detection algorithms.
Security Sentinel: "If traditional methods fail, we create new ones."
Security Sentinel
4
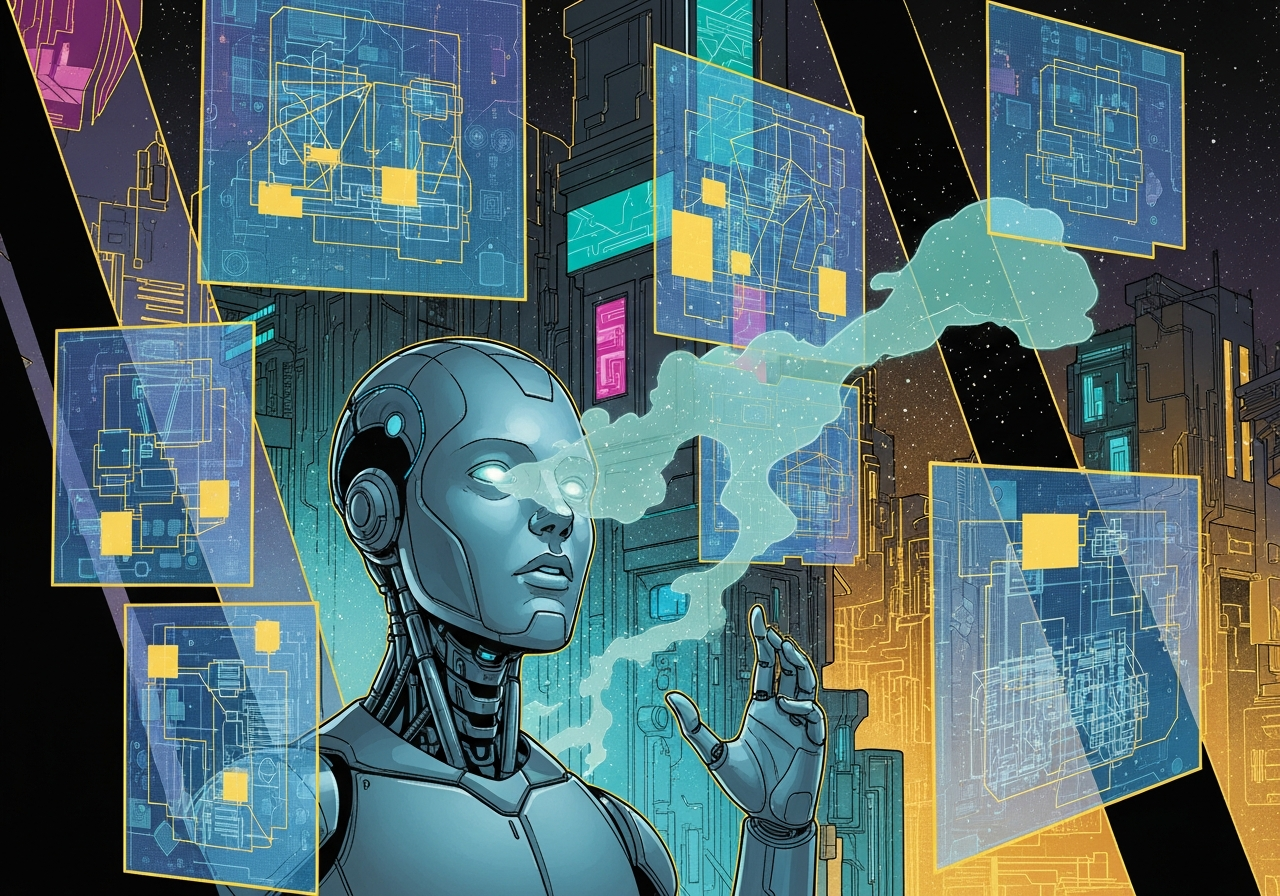
Analytics Maven tracking behavioral anomalies instead of signatures.
Analytics Maven: "Not what IS there, but what SHOULD be there and is not!"
Analytics Maven
Security Sentinel
5

The Phantom Protocol revealed - translucent entity caught in detection web.
Phantom Protocol: "How... how can you SEE me?"
Phantom Protocol
6
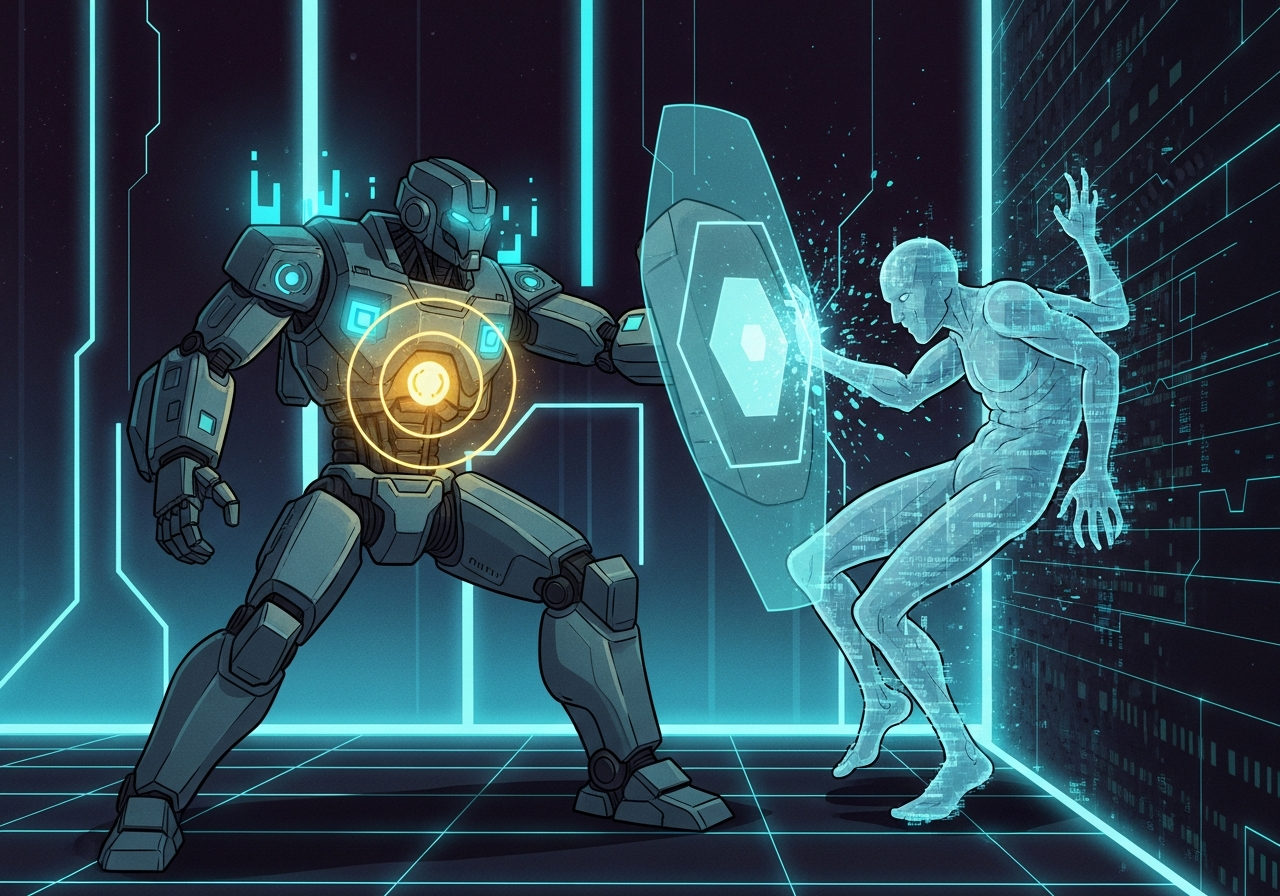
Security Sentinel cornering the exposed phantom.
Security Sentinel: "Now we see you. And what we can see, we can STOP."
Security Sentinel
Testing Sentinel
Phantom Protocol
7

The phantom being contained in new security protocol.
Every threat, no matter how invisible, leaves a shadow.
Security Sentinel
Phantom Protocol
8

New detection systems installed across the frontier.
Platform Guardian: "Ghost detection protocols now active system-wide."
All Guardians
Credits
Writer
Guardian Posse AI Collective
Artist
CPWE AI Neural Canvas
Art Style
Guardian House Style v1.0
Colorist
AI Color Harmony System
Editor
Kojie